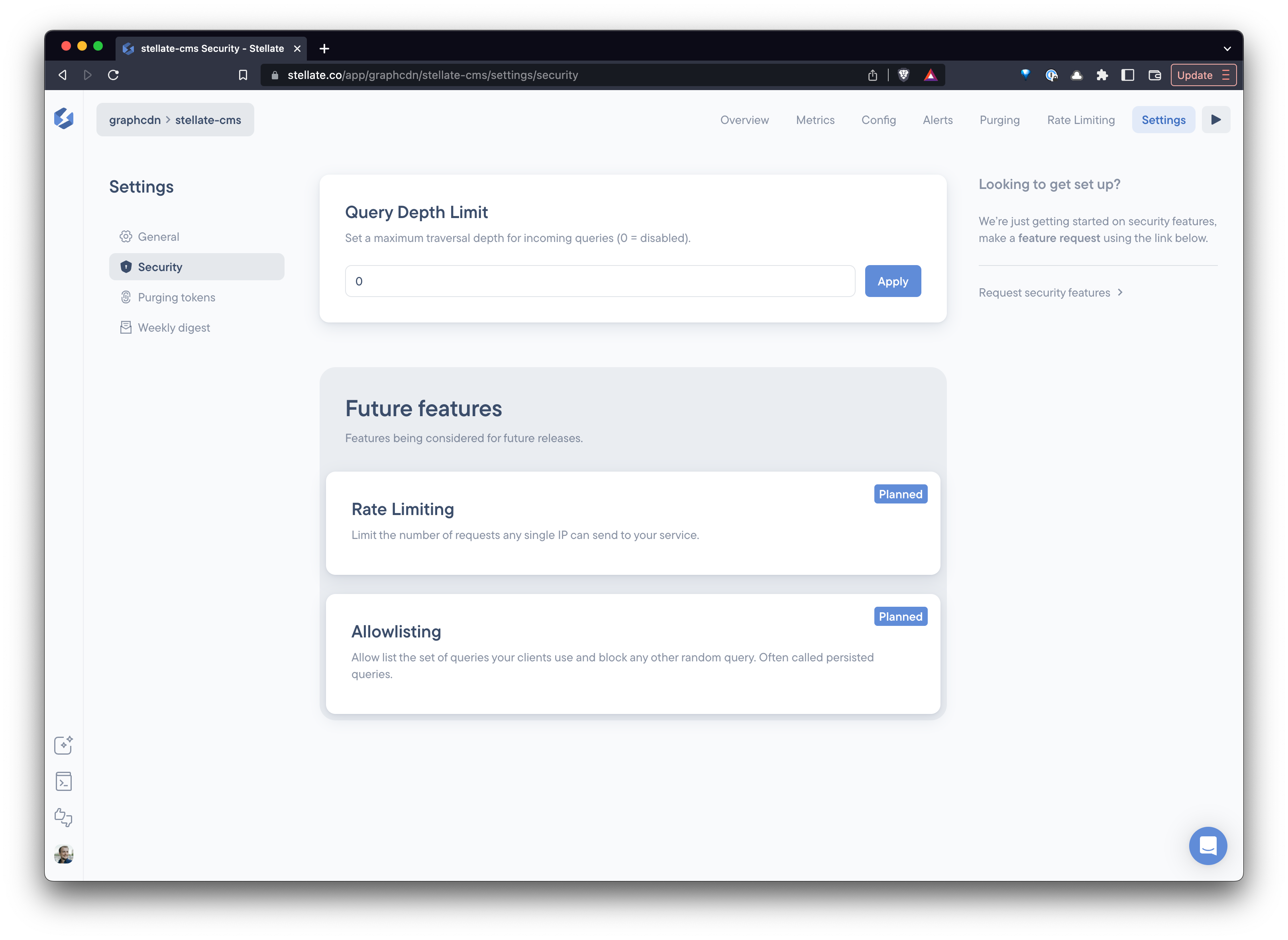
Depth Limiting
One of the most common attacks malicious actors do to GraphQL APIs is sending deeply nested queries to overload the server and/or database. For example, imagine a CMS with a Post that has Comments:
query maliciousQuery {
allPosts {
comments {
post {
comments {
post {
comments {
post {
# ...repeat times 10000...
}
}
}
}
}
}
}
}
DataLoader can prevent some of these queries from taking up too many server resources, but not all of them.
Stellate analyzes incoming queries and blocks them if they are nested too deeply. Since the Stellate Edge Cache sits at the edge, your origin server will never have to deal with these malicious queries!
You can configure your service's query depth limiting on the "Security" tab of the dashboard.