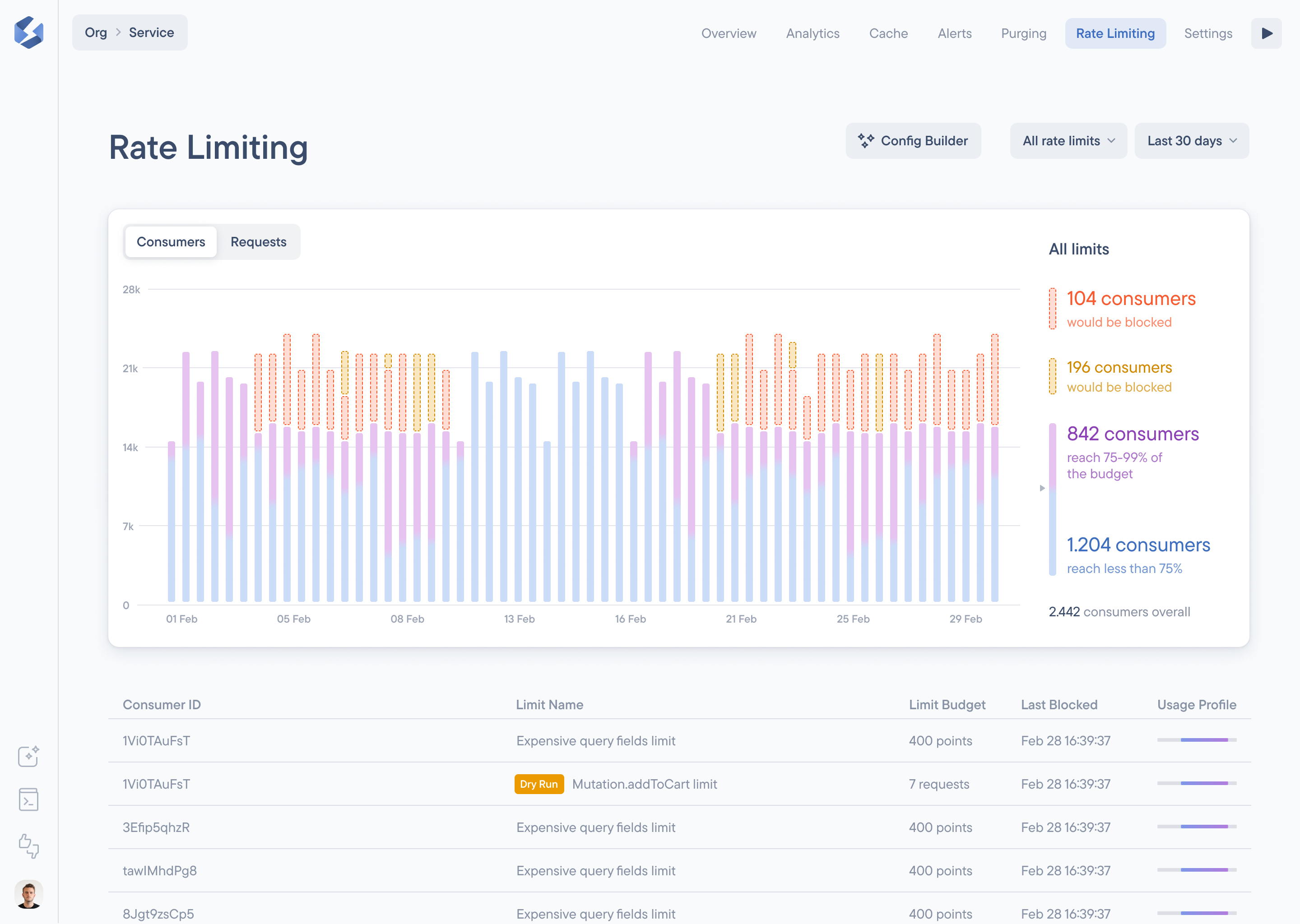
About Rate Limiting
Rate limiting in the context of Stellate is a crucial feature designed to protect GraphQL APIs from unintended or resource-intensive requests. It serves as a tool to rate limit the number of calls any single user can make to an API within a given time frame. By setting up rate limits, you can prevent abuse, ensure fair resource allocation among users, and maintain the health and availability of your services.
Benefits of Rate Limiting
Stellate Rate Limiting offers the following advantages when using GraphQL:
- Prevent API Abuse: Rate limiting helps in preventing users from making too many requests in a short period, which could lead to abuse or even denial-of-service attacks.
- Resource Management: It ensures that resources are evenly distributed among consumers, preventing a single user from monopolizing the API.
- Improved Service Availability: By controlling the traffic flow to the API, rate limiting helps in maintaining the service's availability even during peak times.
- Cost Control: It can help in controlling operational costs by preventing overuse of the API, which might otherwise lead to increased server load and costs.
- Security: Rate limiting can act as a first line of defense against various security threats such as brute force attacks.
Rate Limiting Features
You can take advantage of the following features when using rate limiting:
- Allow Listing: Specific identifiers can be allow-listed to bypass rate limits, suitable for trusted consumers or internal services. Read Rate Limiting Cookbook for details.
- By Query or Mutation: Rate limiting can be applied specifically to certain queries or mutations, allowing for granular control over more expensive operations. Read By Query or Mutationfor implementation details.
- Complexity-Based Limiting: In addition to request count, you can limit based on the complexity of the queries, providing a more nuanced approach to rate limiting. Read Complexity Based Limitingfor implementation details.
- Config Builder: Stellate provides a Config Builder to help you create and manage your rate limiting configuration with ease. Read Config Builderfor implementation details.
- Custom Consumer Identifiers: You can define custom identifiers for consumers based on IP, headers, cookies, JWTs, or any request property to apply rate limits. Read Rate Limiting Cookbookand Rate Limiting API Referencefor more details about custom consumer identifierers.
- Debugging Functions: Functions are available to help you debug and test your rate limiting setup directly from the Stellate dashboard. Read Debugging Functionsfor implementation details.
- Different Rate Limiting Plans: Rate limits can be set differently for authenticated versus unauthenticated users, or for different user plans (free vs. paid). Read the Rate Limiting Cookbook for instructions.
- Global Limits: Set a global limit that applies to all users of an API, useful for managing overall service load. Read the Rate Limiting Cookbook for instructions.
Before You Start
Before you can use rate limiting, you need to set up a Stellate service. Other considerations, when using rate limiting, include:
- Latency Consideration: Enabling rate limiting may increase latency by approximately 20ms, so this should be factored into performance considerations.
- Exclusions: If using Server-Side Rendering (SSR) or Static Rendering, make sure to exclude your builds from rate limiting.
- Proxy Configuration: If a proxy is used in front of Stellate, the correct IP should be configured to ensure accurate rate limiting.
- Dry Run Mode: Starting with rate limiting in dry run mode allows you to inspect traffic without blocking requests, helping you to fine-tune your rules.